Vulnerability Assessment
A vulnerability assessment is a systematic review of security weaknesses in an information system. It evaluates if the system is susceptible to any known vulnerabilities, assigns severity levels to those vulnerabilities, and recommends remediation or mitigation, if and whenever needed. We help many organizations design and implement cloud security controls.
Host Assessment: The assessment of critical servers, which may be vulnerable to attacks if not adequately tested or not generated from a tested machine image.
Database Assessment: The assessment of databases or big data systems for vulnerabilities and misconfigurations, identifying rogue databases or insecure dev/test environments, and classifying sensitive data across an organization’s infrastructure.
Application Scans: The identifying of security vulnerabilities in web applications and their source code by automated scans on the front-end or static/dynamic analysis of source code.c
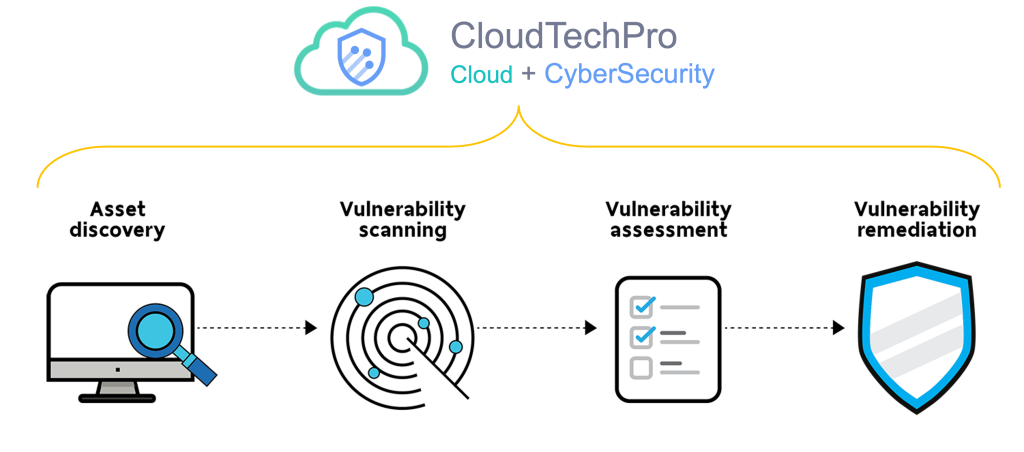
1. Vulnerability identification: The objective of this step is to draft a comprehensive list of an application’s vulnerabilities. Security analysts test the security health of applications, servers or other systems by scanning them with automated tools, or testing and evaluating them manually. Analysts also rely on vulnerability databases, vendor vulnerability announcements, asset management systems and threat intelligence feeds to identify security weaknesses.
2. Vulnerability Analysis: The objective of this step is to identify the source and root cause of the vulnerabilities identified in step one. It involves the identification of system components responsible for each vulnerability, and the root cause of the vulnerability. For example, the root cause of a vulnerability could be an old version of an open source library. This provides a clear path for remediation – upgrading the library.
3. Risk Assessment: The objective of this step is the prioritizing of vulnerabilities. It involves security analysts assigning a rank or severity score to each vulnerability.
4. Remediation: The objective of this step is the closing of security gaps. It’s typically a joint effort by security staff, development and operations teams, who determine the most effective path for remediation or mitigation of each vulnerability.
Appoint us as your valuable cloud experts.
Let us scale your online business together!
Get Started Now

CloudTechPro
Company
Services
Others
Reliable cloud and cybersecurity partners to support your business growth in the technology era.
Reach out to us:
contact@cloudtechpro.com.hk
Copyright © 2023 CloudTechPro Limited. All Rights Reserved.

